Cloud Baseline: Provision well-architected secure AWS environment, ready for production load under 30 minutes
- Santhanam Sivan
- Oct 1, 2024
- 3 min read
Updated: May 3, 2025
As organizations embrace cloud environments, managing account provisioning and its consistency of security standards and policies across AWS accounts become complex and challenging. By combining the strengths of AWS native services like AWS Control Tower, SecurityHub, AWS Config and System manager we can achieve well architected multi-account AWS environment with Automated Security Response(ASR).
AWS Control Tower simplifies the setup and governance of a secure, multi-account AWS environment. It provides a pre-configured landing zone, automated guardrails, and continuous monitoring to ensure your cloud infrastructure remains secure and compliant.
Landing Zone Setup: Deploys a secure, multi-account AWS environment with best practices built-in.
Guardrails: Enforces governance through pre-configured policies and controls.
Automation: Streamlines account creation and configuration processes.
Integrated Monitoring: Works with AWS services like CloudTrail and Config for enhanced visibility.
AWS Security Hub is a security management service that provides a comprehensive view of your cloud environment's security posture. It aggregates, organizes, and prioritizes security findings from various AWS services and third-party tools, giving you actionable insights in one centralized dashboard.
Consolidated Findings: Collects security alerts from services like Amazon GuardDuty, AWS Config, and AWS Firewall Manager.
Compliance Standards: Continuously monitors your environment against compliance frameworks like CIS AWS Foundations Benchmark and PCI DSS.
Automated Response: Integrates with AWS Lambda to enable automated responses to security findings.
Cross-Account Visibility: Offers a unified view of security data across all your AWS accounts.
Security Hub and Control Tower Working Together
AWS Security Hub and AWS Control Tower complement each other to provide a seamless governance and security solution:
Key Benefits:
Automated Account Configuration: Act like a AWS account vending machine aka 'Custom Account Factory' - an abstraction to programmatically provision AWS accounts with this standardized account provisioning makes it easy to automate account baseline procedures.
Guardrails Compliant : Automated deployment of guardrails for multi-account environment. This encompass preventive and detective controls.
Centralized Dashboard: For monitoring multi-account, multi-region compliance score in one-place (Custom CloudWatch Dashboard)
AWS Control Tower and AWS Security Hub are "powerful twins" in securing AWS platform
Architecture Diagram for Provisioning AWS account via Customization for ControlTower (CfCT) Pipeline
Customizations for AWS Control Tower (CfCT) helps you customize your cloudbaseline and stay aligned with AWS security best practices. Customizations are implemented with AWS CloudFormation templates and service control policies (SCPs).
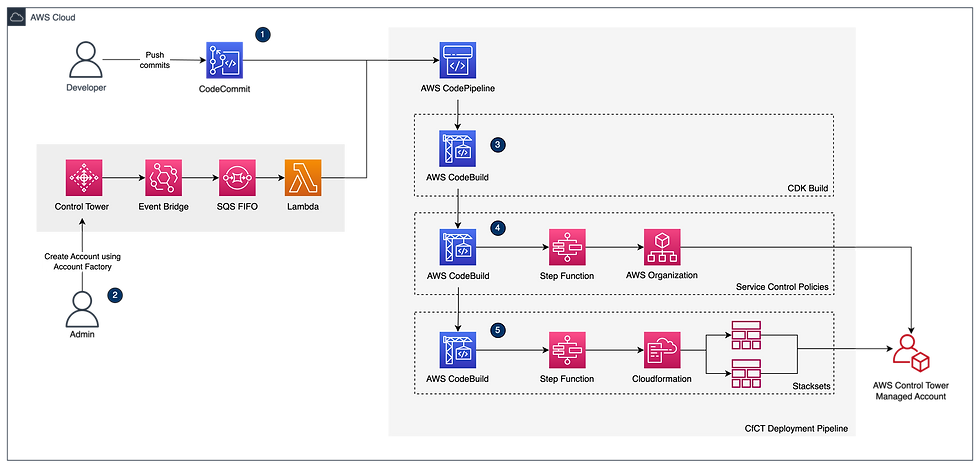
Here is the overview of how the solution works:
Provision AWS account via Cloud formation template or
Accounts can be provisioned via Account Factory as well, AWS codepipline triggered via step-1 or step-2.
Codebuild synthesizes the CDK into cloudformation template and runs the template validation.
Stepfunction (Orchestrated Series of Lambda functions) triggers to apply the Service Control Policies(SCP) for the organization.
Stepfunction trigger the series of cloudformation templates for deploying security control policies (preventive) via substacks.
Automated Security Response(ASR):
ASR automatically address the common security issues across your AWS accounts. When Security Hub identifies a potential security concern, this solution initiates pre-defined responses to resolve the issue efficiently.
Solution:

Steps:
AWS Config service evaluates security rules and send the findings to Security Hub.
Eventbridge gets triggered based on type of failed findings in securityhub.
2a - New findings - direct trigger 2b - Existing findings - custom action trigger
Event rule trigger the statemachine
Statemachine triggers lambda function - to assume roles to act on the resources.
Remediation actions are performed based on the remediation document built for security control.
SSM (System Manager) automation updates security hub with remediation results and update the findings in SecurityHub.
ASR action and results get notified based on notification subscription.
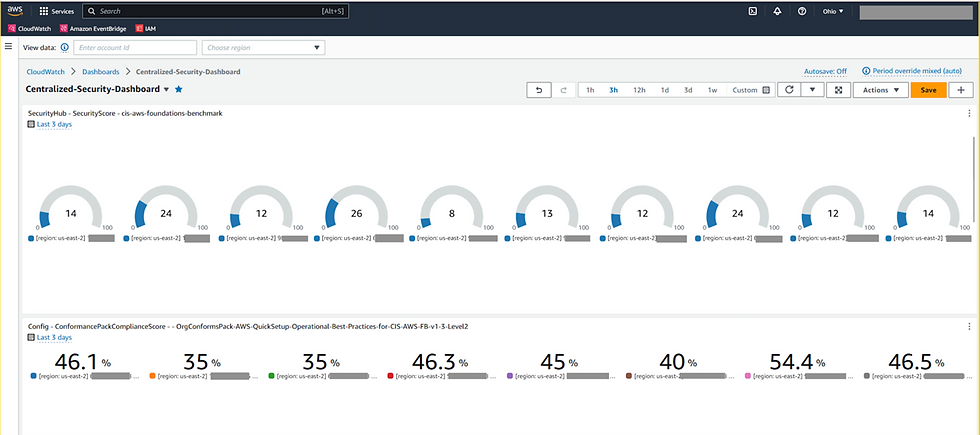
Centralized Security Dashboard:
Using cloudwatch custom metrics, we can create a centralized security dashboard which show Security sores across accounts and regions.
Conclusion
With tailored account baseline procedures, we simplify AWS account provisioning and enforce adherence to cloud security standards which ensure AWS accounts are in compliance with regulatory requirements from day-1.
Do you need to streamline your AWS account provisioning with baseline security and governance? Just drop a one liner email to us - info@inayam.consulting, we can support you to achieve the goal quicker.



Comments